Inline SSL Decryption Deployments
There are two ways to deploy inline SSL decryption as follows:
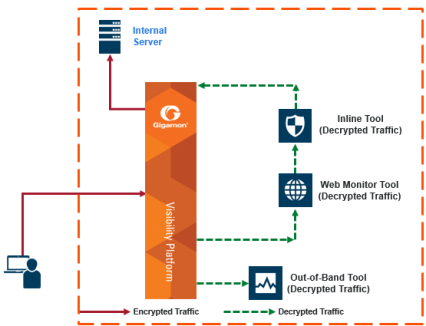
Refer to Figure 1: Inbound Deployment of Inline SSL Decryption for an example of an inbound deployment. The client is on the Internet. The server and the GigaVUE node are located within the same enterprise network, with the GigaVUE node deployed on the server side. The GigaVUE node needs access to the private keys of the server to perform Man-in-the-Middle (MitM) decryption.
|
Figure 103
|
Inbound Deployment of Inline SSL Decryption |
Use case for inline SSL decryption:
|
•
|
Clients on the Internet |
|
•
|
Servers in internal network |
|
•
|
Organization has the private key of the server |
|
•
|
Diffie-Hellman and Perfect Forward Secrecy is being used |
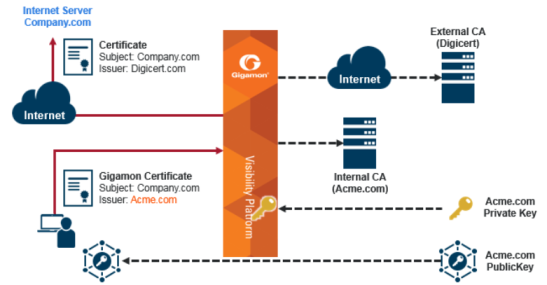
Refer to Figure 2: Outbound Deployment of Inline SSL Decryption for an example of an outbound deployment. The client and the GigaVUE node are located within the same enterprise network, with the GigaVUE node deployed on the client side. The server is located in another network on the Internet. In this deployment, the role of the GigaVUE node is that of a Man-in-the-Middle (MitM). In this deployment, the GigaVUE node does not have access to the private keys of the server, but as a trusted MitM, the GigaVUE node can look at SSL traffic.
|
Figure 104
|
Outbound Deployment of Inline SSL Decryption |





