Controlled GigaStream
Controlled GigaStream provides controlled traffic distribution, which gives more granular control over hashing to the tool ports.
All GigaVUE H Series and TA Series nodes support controlled GigaStream.
GigaVUE nodes with controlled GigaStream are supported in a cluster environment.
Controlled GigaStream can only be used as a packet egress destination (tool GigaStream). All port speeds are supported.
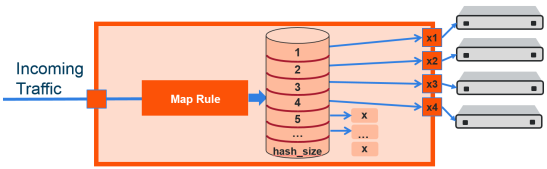
With controlled GigaStream, the hashing is computed based on traffic. There is a configurable number of hash buckets, from 1 to 256. The hash size of a controlled GigaStream specifies the number of logical tools the traffic will be distributed across. Refer to Figure 1 Controlled GigaStream Overview.
| Figure 20 | Controlled GigaStream Overview |
Controlled GigaStream can manage network port bandwidth hashed to GigaStream tool ports. For example, if there is 10Gb of distributed traffic coming in on network ports directed to a GigaStream, and the tools connected to each tool port of the GigaStream can handle only 2Gb of bandwidth, the GigaStream can distribute the streams to 5 tool GigaStream ports. The ingress bandwidth divided by the number of tools determines the number of hash buckets.
Not all hash buckets need to be mapped to ports. In Figure 1 Controlled GigaStream Overview, four buckets are mapped to ports, while the remaining buckets are black holed. This provides a form of sampling, that is, only a sample of traffic is sent to the tools.
To determine the best hash size to use for your monitoring needs, divide the maximum bandwidth being sent to the tools by the bandwidth that can actually be consumed by the tools. For example, if you have 150 Gb of traffic, but the tools can only process 3 Gb, the recommended hash size is 150/3 = 50. To have completely even distribution across the logical tools, round up to the nearest power of 2. In this example, round up a hash size to 64.
When you have more bandwidth than the tools can process, you can use controlled GigaStream to restrict the amount of traffic sent to each tool. The hash size is determined by:
| • | the amount of traffic to be monitored, for example 300Gb |
| • | the maximum bandwidth of the monitoring tools, for example 2.5Gb |
Then divide (300/2.5=120), and round up to a power of 2 (for example, 16, 32, 64, 128). In this case, the hash size would be 128.
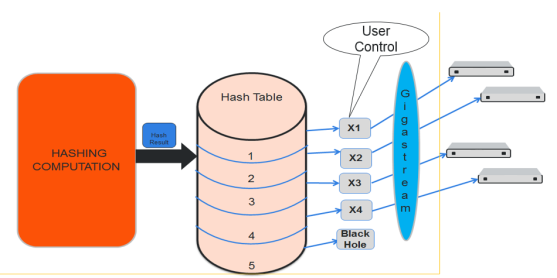
Another use for a controlled GigaStream is to increase the reliability of tool ports. For example, a trunk size of 5 is configured on 4 ports with 1 hash bucket each, port x1 is allocated or mapped to hash bucket ID 1, port x2 is mapped to hash bucket ID 2, port x3 is mapped to hash bucket ID 3, and port x4 is mapped to hash bucket ID 4. Hash bucket ID 5 is not mapped to a port. It can be reserved to be mapped to a port later. Until then, any traffic hashed to bucket 5 will be black holed. Refer to Figure 2 Controlled GigaStream Example.
| Figure 21 | Controlled GigaStream Example |
Generally, if there are only four tools available, with controlled GigaStream, a GigaStream trunk size of 5 can be configured and allocated to the available four tool ports of the GigaStream. The fifth tool port can be reserved and you can attach that port to the GigaStream whenever it is needed. The existing traffic streams are not impacted.
GigaStream controlled traffic distribution provides enhanced control of traffic hashed across the trunk ports as compared to regular GigaStream. The GigaStream trunk size is configurable, and ports can be dynamically added and deleted.
To configure controlled GigaStream, there are two parameters needed as follows:
| • | the hashing trunk size, which defines the number of hash buckets to be configured. It defines the maximum number of hash bucket IDs, from 1 to 256. |
| • | the hash bucket ID, which specifies the mapping to ports. Each member of the trunk is mapped to a hash bucket ID. Mapping a port to a hash bucket ID makes it part of a GigaStream. The mapping to ports is static. When a port goes down, traffic is not re-hashed to the remaining ports. |
In general, a controlled GigaStream is defined with a hash size equal to the number of trunk ports expected. Mapping a hash bucket ID to each trunk port will evenly distribute the traffic among the ports.
A particular trunk member can be mapped to multiple hash bucket IDs. If one tool can handle 4Gb, 2 hash bucket IDs can be mapped to that tool port. A trunk member that is configured to two hash bucket IDs will be two times more likely to receive hashed traffic as compared to a trunk member with one hash bucket ID. Thus, more traffic can be sent to the higher capacity tools in the GigaStream.
Note: A hash bucket ID cannot be mapped to multiple ports.
For more information, refer to Traffic Distribution Across Controlled GigaStream.
Notes and Considerations for Controlled GigaStream
Refer to the following notes and considerations for controlled GigaStream:
| • | Controlled GigaStream can be used with a regular map, map-passall, or map-scollector. |
| • | Controlled GigaStream supports tool ports, but not inline tools or inline tool groups. |
| • | Controlled GigaStream does not support stack or hybrid port types. |
| • | Controlled GigaStream does not support a GigaSMART operation (gsop), or the first and second level maps associated with it. |
| • | The maximum hash size is 256 per trunk. |
| • | All the tool ports participating in the GigaStream must be on the same node. GigaStream can be created across GigaVUE-HC2 or GigaVUE-HC3 modules. |
| • | All participating ports in the GigaStream must be running the same speed and must use the same port type. |
| • | A Controlled GigaStream checkbox is used on the GigaStream configuration page for controlled GigaStream, enabling the prefix mode for specifying hash size and hash bucket IDs. |
| • | Before attaching a controlled GigaStream to a map, it should be configured with at least one port. |
| • | Controlled GigaStream can be modified on the fly, even after it is attached to a map. Refer to Edit Regular GigaStream. |
| • | If the GigaStream is already attached to a map, the last mapped hash bucket ID cannot be deleted. That is, do not delete all the ports from a controlled GigaStream. |
Controlled GigaStream Configuration
To configure a controlled tool GigaStream, specify hash size and hash bucket ID.
Following are the steps to configure Controlled GigaStream:
| 1. | Use the Quick Port Editor to configure ports as type tool for the controlled GigaStream. |
| 2. | Select Ports > Port Groups > GigaStreams and click New to open the GigaStreams configuration page. |
| 3. | Enter an name for the GigaStream in the Alias field. For example stream 2. |
| 4. | (Optional) Enter a comment in the Comment field. For example, controlled GigaStream. |
| 5. | For Type, select Tool GigaStream. |
| 6. | Select Controlled GigaStream. The Port field changes to Hash Size. |
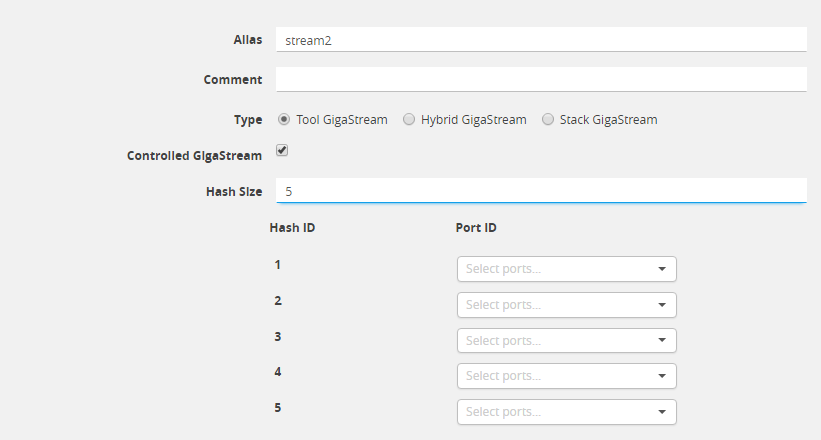
| 7. | In the Hash Size field, specify a hash size value. The range is 1 through 256. |
The hash size value determines the number of hash bucked IDs and ports available for assigning to the GigaStream. For example, in Figure 3 Controlled GigaStream with Five Hash IDs and Port IDs, the Hash Size is set to 5 so the GigaStream page displays five Hash IDs and five Port ID fields.
| Figure 22 | Controlled GigaStream with Five Hash IDs and Port IDs |
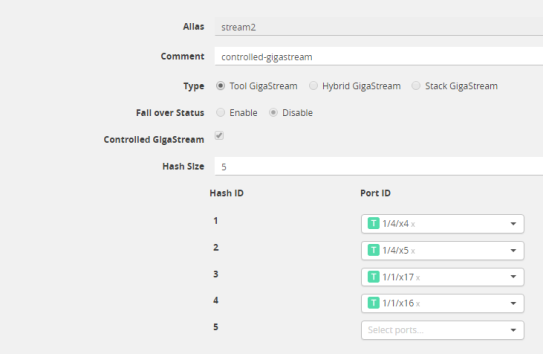
| 8. | Assign ports to the hash bucket IDs by clicking in each Port ID field and selecting a tool port. |
The example in Figure 4 Ports Assigned to Hash Bucket IDs assign tool ports to hash buckets 1 though 4. Hash bucket 5 has no port assigned to it.
| Figure 23 | Ports Assigned to Hash Bucket IDs |
| 9. | Click Save. |
After saving the controlled GigaStream, it appears on the GigaStreams page.
Note: For controlled GigaStream, the GigaStream page shows a Failover Status of disabled. When a port goes down, traffic is not re-hashed. Refer to Failover and Controlled GigaStream.
Edit Controlled GigaStream
A controlled GigaStream can be edited, even when the GigaStream is attached to a map. Unlike regular GigaStream, you can make changes without deleting the map or the GigaStream.
You have the control to map unused hash bucket IDs to any tool port dynamically, without deleting the trunk. This modification of a tool port mapping to a hash bucket ID will not affect the streams flowing on the hash bucket IDs that are mapped to other ports. In addition, you can replace the mapping of any hash bucket ID to a port, dynamically.
If one of the GigaStream ports goes down, all the hash bucket IDs mapped to that port will be black holed until they are re-mapped to a new port, or until the port comes back up. This means that the packets sent to the remaining tools are unaffected.
If one port is receiving a lesser amount of bandwidth, the traffic can be reallocated to it. For example, if port x4 is underutilized, you have the control to reconfigure hash bucket ID 5 to also map to port x4. Then port x4 receives all the traffic that is hashed to hash bucket IDs 4 and 5.
You also have the flexibility to change the size of the trunk anytime, but this will require reprogramming of the whole hash table, so that might impact the existing streams.
Increasing the size of the trunk creates new hash buckets, which can be mapped to new or existing GigaStream tool ports. You can increase the bucket size per GigaStream. For example, if the bucket size is 4, you can increase it to 5.
If the size of the trunk has to be decreased, you have to take extra caution when releasing the hash bucket IDs gracefully, since they are mapped to GigaStream tool ports.
If you decrease the bucket size, empty out the bucket by unmapping buckets to ports. Also, do not reduce the hash size to less than the last occupied hash bucket ID.
Note: There is some packet drop associated with the following type of controlled GigaStream editing:
| • | adding a new port |
| • | deleting an existing port |
| • | changing the hash size |
The Port Statistics page may display Discards in these cases, but not when additional buckets are added to the same port, or when a port goes down.
Traffic Distribution Across Controlled GigaStream
Controlled GigaStream has N buckets (where N is from 1 to 256) distributed across one or more ports, logical or physical.
Controlled GigaStream uses advanced hashing with 1 to 256 buckets. With controlled GigaStream, you define the number of buckets first, unlike with regular GigaStream.
Controlled GigaStream can manage network port bandwidth hashed to GigaStream tool ports. For example, if you are monitoring 500Gb traffic and have 10 tools, 50Gb per tool would be required. But if the tools cannot handle 50Gb, packets will be lost randomly.
With controlled GigaStream, first determine how much traffic the tools can process. For example, perhaps each tool can process 5Gb of traffic.
The formula is ingress bandwidth divided by tool capability. For example, 500Gb/5Gb = 100 tools. But if you only have 10 tools, you create a controlled GigaStream of 100 logical tools or 100 logical hash buckets, and then map only 10 of them.
Taking the number of buckets and dividing it by 100 tools (256/100 = 2.56) results in some buckets of 3, some buckets of 2.
The recommendation is to round to an even divisor of 256 (2, 4, 8, 16, 32, 64, 128, or 256). In this example, instead of using 100, use 128, so each bucket will be 2 (256/128 = 2).
Hash buckets IDs are mapped to ports as follows:
|
Buckets |
Ports |
|
1 |
x1 |
|
2 |
x2 |
|
3 |
x3 |
|
4 |
x4 |
|
5 |
x5 |
|
6 |
x6 |
|
7 |
x7 |
|
8 |
x8 |
|
9 |
x9 |
|
10 |
x10 |
|
11 |
unmapped |
|
... |
unmapped |
|
128 |
unmapped |
The hashing to the 10 connected tools captures the traffic associated with those sessions.
There are no tools associated with the remaining buckets, so that traffic is black holed. Unlike regular GigaStream, you do not have to allocate ports to the remaining buckets.
Multiple buckets can be mapped to one physical port as follows:
|
Buckets |
Ports |
|
1 |
x1 |
|
2 |
x1 |
|
3 |
x2 |
|
4 |
x3 |
|
... |
... |
In this example, port x1 receives 5Gb of traffic, while ports x2 and x3 receive 2.5Gb each.
Note that the mapping does not have to be consecutive as follows:
|
Buckets |
Ports |
|
1 |
x1 |
|
2 |
x2 |
|
3 |
x3 |
|
4 |
x1 |
|
... |
... |
In this example, port x1 also receives 5Gb of traffic, while ports x2 and x3 receive 2.5Gb each.
Through the mapping of buckets to ports, you can control the overall distribution of traffic to a given port.
Failover and Controlled GigaStream
Unlike the regular GigaStream, failover will not be triggered during a port down event. With controlled GigaStream, there is no rehashing or redistribution of traffic. In other words, the sessions flowing to other tool ports will not be disturbed and do not risk becoming oversubscribed.
Controlled GigaStream maintains hashing. When a port goes down, traffic is not re-hashed, but is black holed. Unlike with regular GigaStream, you do not need to enable Force Link Up on ports in order to counteract the default failover protection.



